Verifying the Physical World: Witness Chain and Proof of Location on EigenCloud
Introduction
Proof of Location (PoL) is a cryptographic technique used to verify that a device or service provider was physically present at a specific location and time. Unlike GPS or WiFi-based systems, which rely on self-reported data or centralized infrastructure, PoL provides verifiable evidence that can be independently checked and used to trigger smart contracts or validate claims.
Traditional location systems are vulnerable to spoofing and manipulation. GPS signals can be faked, and applications often accept location data without verification. This creates problems in systems where trust and accuracy are essential, such as decentralized storage, autonomous delivery, or compliance with geographic regulations.
Proof of Location addresses these issues by enabling location claims to be validated through cryptographic or network-based methods. These claims can then be used in automated systems that rely on physical context, such as releasing payment when a package reaches its destination, enforcing local energy trading rules, or verifying that compute tasks are performed in approved jurisdictions. As physical infrastructure becomes increasingly decentralized and automated, the need for verifiable location data will continue to grow. Trust-free PoL protocols offer a foundation for ensuring accountability, enforcing contracts, and preventing fraud in systems that cannot rely on centralized oversight.
The Need for Verifiable Location
Most systems that rely on location data today operate on a model of implicit trust. Whether it is a phone sharing its coordinates with a navigation app or a delivery service marking a package as dropped off, the system assumes the location information is accurate. In many cases, this is good enough. But in environments where location is tied to payments, compliance, or security, unverifiable claims create opportunities for fraud and system failure.
Spoofing is a widespread vulnerability. GPS signals can be manipulated with off-the-shelf tools or mobile apps, allowing users to falsify their whereabouts. There are documented cases of drivers faking routes to increase earnings, players cheating in location-based games, and individuals spoofing attendance at physical locations to trigger benefits or permissions. These weaknesses make current systems unsuitable for settings where location has direct financial or operational consequences.
The risk increases in automated or decentralized systems. Without a central entity to validate claims, self-reported location data becomes an easy target for manipulation. Fraudulent actors can claim to be in multiple places at once, operate outside permitted zones, or exploit incentive models that reward participation in specific regions. The inability to verify these claims undermines trust and limits the kinds of applications that can be deployed at scale.
Proof of Location addresses this problem by introducing a verifiable, cryptographically-backed way to confirm physical presence. It eliminates the need to trust the device or the user and instead allows the system to rely on independent verification. This foundational capability enables a wide range of applications that depend on geographic context, from autonomous service execution to compliance enforcement.
Why Witness Chain Matters
Witness Chain addresses a core limitation in the DePIN landscape: the lack of verifiable, trustless geolocation. In decentralized networks offering compute, storage, bandwidth, or energy services, location is more than a convenience; it determines pricing, regulatory compliance, redundancy planning, and user access. Without robust location proofs, networks become vulnerable to Sybil attacks, false redundancy claims, and jurisdictional evasion.
Witness Chain provides an onchain, cryptographically verifiable solution that integrates seamlessly into smart contracts. Verified location data can trigger payments, authorize service access, or enforce energy trading rules. In practice, this can enable a compute job to be automatically routed only to nodes in a specific jurisdiction, or a solar power seller to be compensated only if their panel is in a verified high-demand zone.
The protocol's modularity makes it adaptable across sectors. For example:
- Compute networks can ensure low-latency task assignment based on proximity.
- Storage networks can enforce geospatial data replication policies.
- Energy systems can enable localized pricing and grid balancing.
- Wireless networks can allocate spectrum more efficiently based on active, verified nodes.
By anchoring physical presence to blockchain-based logic, Witness Chain expands the programmable surface area of smart contracts to include geography itself.
Proof of Location in the Verifiable AI Context
In the context of AI, we can discuss at least 3 use cases where Proof of Location is uniquely valuable: social media, sovereign agents, and prediction markets. As people upload images and videos onto social media from across the world, it’s becoming increasingly important to be able to detect whether a post was uploaded from the location that it claimed to be uploaded from.
Take the case of Collective Memory: a social media network where users upload pictures and videos called Memories, each of which comes with the ability for the users of the network to stake into it. If users predict that a certain memory might receive a lot of attention, they can stake into it and share in the upside of that memory becoming more valuable. One measure of making this flow even more robust is having each memory uploaded be tagged by the location from which it was uploaded and have this tag be verified by Proof of Location. This way users who may want to stake into a memory can verify that the content actually came from the claimed location.
Another instance of Proof of Location being useful is for (Sovereign) Agents. If an agent needs to be able to prove to its counterparties (or even to itself) that it’s running in a certain part of the world, Proof of Location can verifiably provide this data. Let’s say an agent is operating in a jurisdiction with specific laws and requires that the other agents it interacts with to also comply with these laws: this agent can ask for Proof of Location from its counterparties as the first step of the interaction before proceeding. This way the agent remains compliant.
At least one more use case is in the context of prediction market settlement. If a condition of market creation is that the market settlement is judged by a verifiable AI, and if the market has other conditions that relate to any physical locations in the world, the data that the verifiable AI can use to make its judgement can use Proof of Location to verify whether that data came from the location it’s supposed to be coming from.
Proof of Location in the DePIN Context
As decentralized infrastructure moves into the physical world, the ability to verify where services are being delivered becomes essential. This is the case with Decentralized Physical Infrastructure Networks, or DePIN. These are blockchain-based systems that coordinate real-world services like file storage, compute power, wireless bandwidth, and energy distribution, all provided by independent node operators.
In DePIN networks, the location of a node directly affects its eligibility, pricing, and function. A compute node in one jurisdiction may be legally allowed to process sensitive data, while one in another may not. A storage provider might only be useful if it offers data redundancy across physical regions. A solar array might only contribute value to a local microgrid if it can prove it is generating power within that grid’s boundaries.
Proof of Location plays a critical role in making these networks work. It ensures that nodes are actually operating where they say they are, preventing actors from spoofing their coordinates to gain access to contracts or rewards. It also protects against Sybil attacks, where a single actor pretends to be many geographically dispersed nodes.
Trustless location verification also enables more advanced coordination. Compute workloads can be routed to nearby nodes to reduce latency. Data can be sharded across physically diverse storage providers to improve resilience. Pricing models for services like GPU compute or energy can adjust based on location-specific demand and supply, enabling more efficient markets.
Without verifiable location, DePIN networks would be forced to rely on trust or central oversight, undermining their core value proposition. Proof of Location provides the foundation for secure, fair, and efficient coordination in systems that operate in both digital and physical space.
Witness Chain: A Trustless Network for Proof of Location
Witness Chain is one of the first implementations of decentralized Proof of Location infrastructure designed to validate geographic claims made by devices providing real-world services. Built for a wide range of Decentralized Physical Infrastructure Networks (DePIN), Witness Chain establishes a system for verifying that nodes (provers) are truly operating from the locations they claim. This location integrity is enforced without relying on centralized authorities, using a network of distributed validators known as watchtowers.
How Witness Chain Works
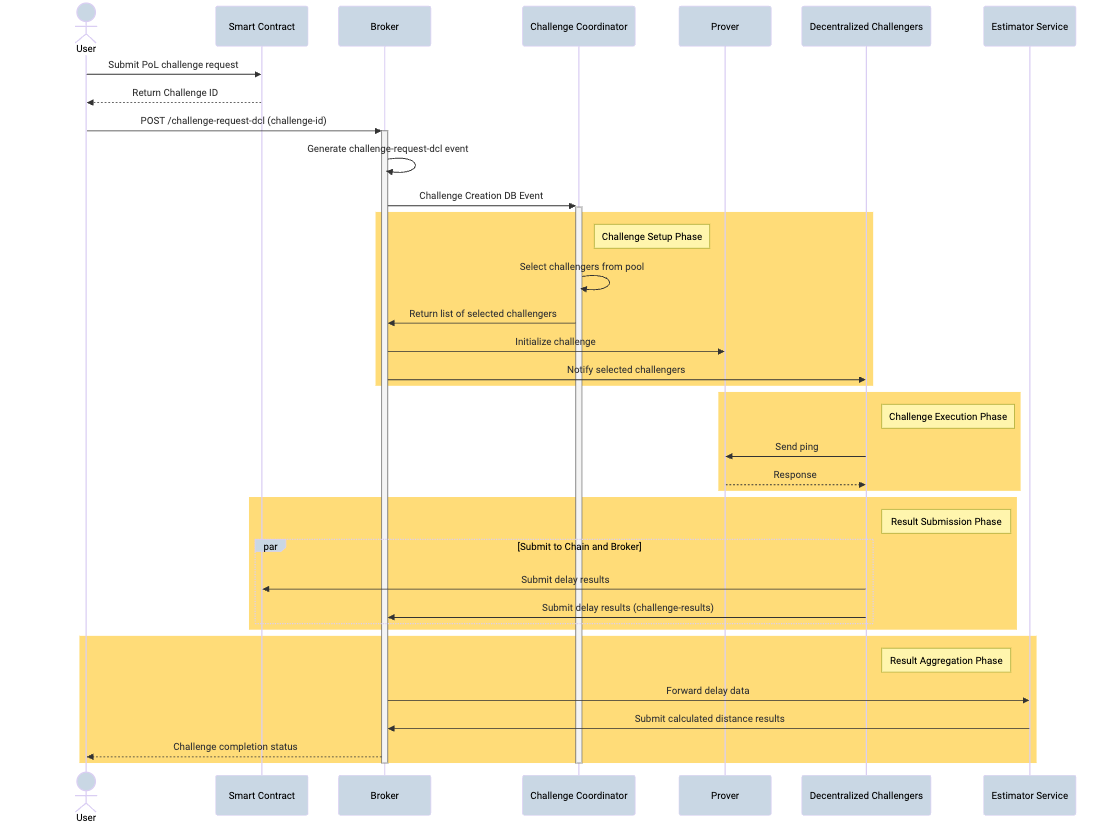
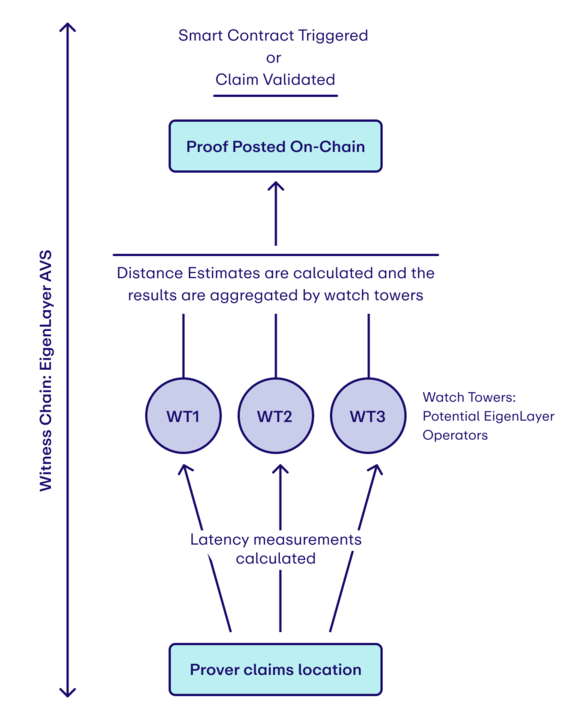
At the core of Witness Chain’s design is a latency-based verification mechanism. Rather than relying on GPS or Wi-Fi signals, which can be spoofed or forged, Witness Chain utilizes network latency measurements between nodes. These latency patterns are used to estimate physical distances between a prover and a set of known-location watchtowers. The system operates in two distinct phases: calibration and measurement.
1. Calibration Phase
In this step, each watchtower pings other watchtowers using application-layer UDP messages to measure baseline latency. Since the geographic locations of the watchtowers are known ahead of time, these round-trip times are converted into distance estimates using delay-to-distance mappings. This calibration enables each watchtower to construct a local model of how latency correlates with distance on the current network, taking into account regional conditions, routing paths, and internet topology.
2. Measurement Phase
Once calibration is complete, the system can evaluate a prover’s location claim. When a prover asserts its location, each selected watchtower sends UDP pings to that prover. Using the previously calibrated model, each watchtower determines a region in which the prover could reasonably exist, given the observed latency. These outputs are aggregated, and the protocol computes a consensus-bound, typically the maximum distance the prover could be from the claimed coordinates. If this bound is within an acceptable error threshold, the location claim is verified.
Participants and Roles
Witness Chain’s protocol relies on multiple stakeholders, each with a defined role in the challenge process:
- Prover: The node asserting a location claim, typically providing a service like storage or compute.
- Watchtowers: Decentralized validators with known locations that conduct latency measurements.
- Payer: The entity requesting a PoL verification and covering its cost.
- Challenge Coordinator: Currently centralized, this service manages communication, coordinates challenges, and interfaces with the blockchain ledger.
- Broker: An API layer facilitating communication between users, the coordinator, and the blockchain.
- Blockchain Full Node: Stores immutable records of challenge requests and outcomes.
Challenger Selection and Network Constraints
To maintain security, fairness, and efficiency, Witness Chain includes a strict set of rules for challenger selection:
- Challengers must be active (i.e., responding within the last 60 seconds).
- Each must have an associated wallet for identification and signing.
- Nodes with private IP addresses can only challenge provers with public IPs.
- The geographic distance between the prover and challengers must not exceed 2000 km.
- Up to 128 challengers can be selected per challenge.
- A node cannot act as both prover and challenger in the same verification.
These constraints are designed to limit the impact of latency anomalies, reduce fraud risk, and prevent location spoofing. While the current implementation uses a centralized coordinator, future versions aim to incorporate fully decentralized challenger selection, including tolerance for a subset of adversarial watchtowers.
Integrating Witness Chain with EigenCloud: Expanding PoL via Restaking Infrastructure
Witness Chain’s Proof of Location protocol requires a robust and distributed network of challenger nodes that can reliably validate geographic claims through latency-based measurements. This demand aligns closely with EigenCloud’s Autonomous Verifiable Service (AVS) model, which provides a decentralized trust layer backed by Ethereum stakers and operated by a permissionless network of restaked nodes. By deploying Witness Chain as an AVS on EigenCloud, the PoL system can scale its verifier network, improve decentralization, and enhance cryptoeconomic guarantees.
Why EigenCloud is a Natural Fit for Witness Chain
EigenCloud enables developers to launch new protocols, like PoL, without having to bootstrap their own security model. Instead, AVSs can tap into the pooled trust of Ethereum by using restaked ETH. This allows services like Witness Chain to:
- Leverage an existing decentralized validator set for watchtower and challenger operations.
- Enforce cryptoeconomic slashing conditions for dishonest or lazy behavior in latency reporting.
- Increase geographic coverage through global EigenLayer node distribution.
- Avoid reliance on a centralized Challenge Coordinator over time.
How EigenLayer Operators Participate in Proof of Location
EigenLayer node operators are well-positioned to run Witness Chain challenger clients with minimal additional setup. The system is lightweight and designed to run even on low-spec machines (e.g., equivalent to AWS t2.micro). These operators can:
1. Register as Challenger Nodes
Operators register with the Witness Chain coordination platform, providing metadata such as geographic coordinates and IP type (public/private). This data is used during challenger selection to filter nodes based on distance, responsiveness, and compatibility.
2. Run Latency Measurements
As part of the PoL process, EigenLayer nodes acting as challengers will:
- Conduct calibration pings with other known-location nodes to establish delay-to-distance mappings.
- Send application-layer UDP pings to prover nodes during challenges.
- Submit encrypted or signed latency data to the coordinator or smart contract for aggregation.
This lightweight validation process has low CPU and bandwidth demands, making it ideal for integration with AVSs where resource constraints are a concern.
3. Earn Rewards for Verification Work
Although payments are not currently active, the protocol is expected to introduce a credit or token-based incentive model. EigenLayer’s native restaking mechanisms make this particularly powerful, as rewards can be distributed or withheld based on uptime, accuracy, and participation quality. Furthermore, slashing mechanisms could be introduced to penalize collusion or misreporting by watchtower nodes.
4. Enhance Cryptoeconomic Security
Because EigenLayer validators have collateral (ETH or LSTs) restaked against their identity, their involvement provides stronger assurances than unaffiliated challengers. If a restaked node participates in a challenge and misbehaves, e.g., by submitting falsified latency data, it could face verifiable consequences enforced at the EigenLayer level.
This alignment of incentives allows PoL services like Witness Chain to go beyond optimistic trust assumptions and enforce adversarial resistance through slashing conditions, similar to how rollups or oracles maintain liveness and honesty guarantees.
Use Cases Unlocked by AVS Integration
With the added security and coverage provided by EigenLayer, Witness Chain could support more critical and high-value use cases, such as:
- Regulatory compliance for location-bound compute in cloud-neutral AI networks.
- Geo-fenced insurance payouts based on verifiable weather or disaster conditions.
- Dynamic pricing for bandwidth or storage based on verified node proximity.
- Jurisdictional restrictions for zero-knowledge applications requiring physical boundaries.
Long-Term Vision: Trustless Location Verification as Public Infrastructure
As an AVS, Witness Chain can function as a public utility layer for decentralized geolocation. Other protocols could consume verified location outputs as oracle-like inputs, allowing smart contracts to interact with real-world spatial data in a permissionless, trust-minimized way.
EigenCloud’s ecosystem also makes it easy to coordinate multi-AVS interactions. For instance, a DePIN project using an EigenCloudAVS for bandwidth or compute metering could cross-reference a Witness Chain AVS to confirm that those services are delivered from approved geographic zones.
Conclusion
Time will ultimately determine the adoption and success of trustless Proof of Location protocols like Witness Chain. However, the technical foundation they offer, particularly when integrated with platforms like EigenCloud, is compelling. As decentralized infrastructure expands into the physical world, the ability to cryptographically verify location may become not just useful, but essential.

